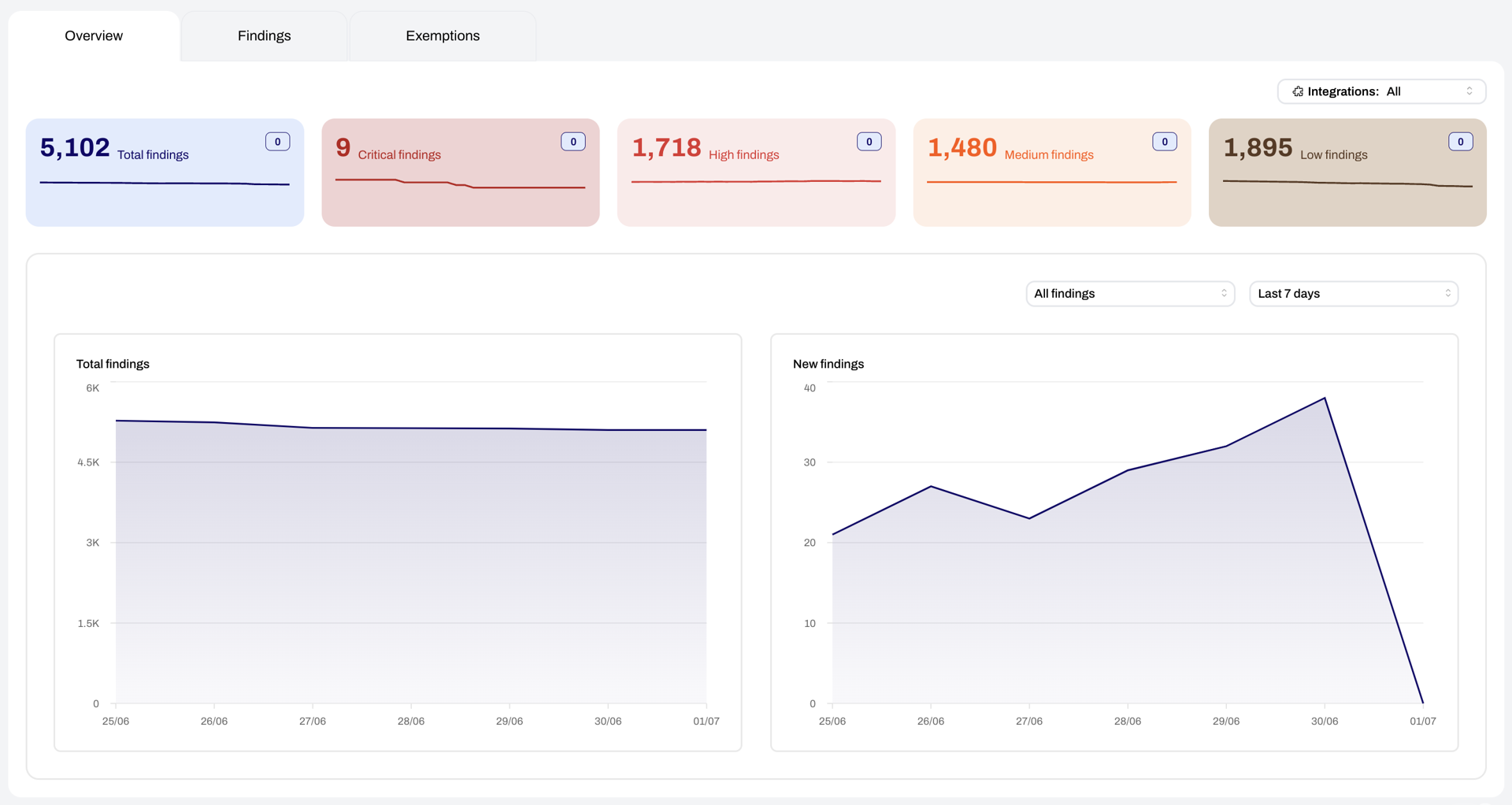
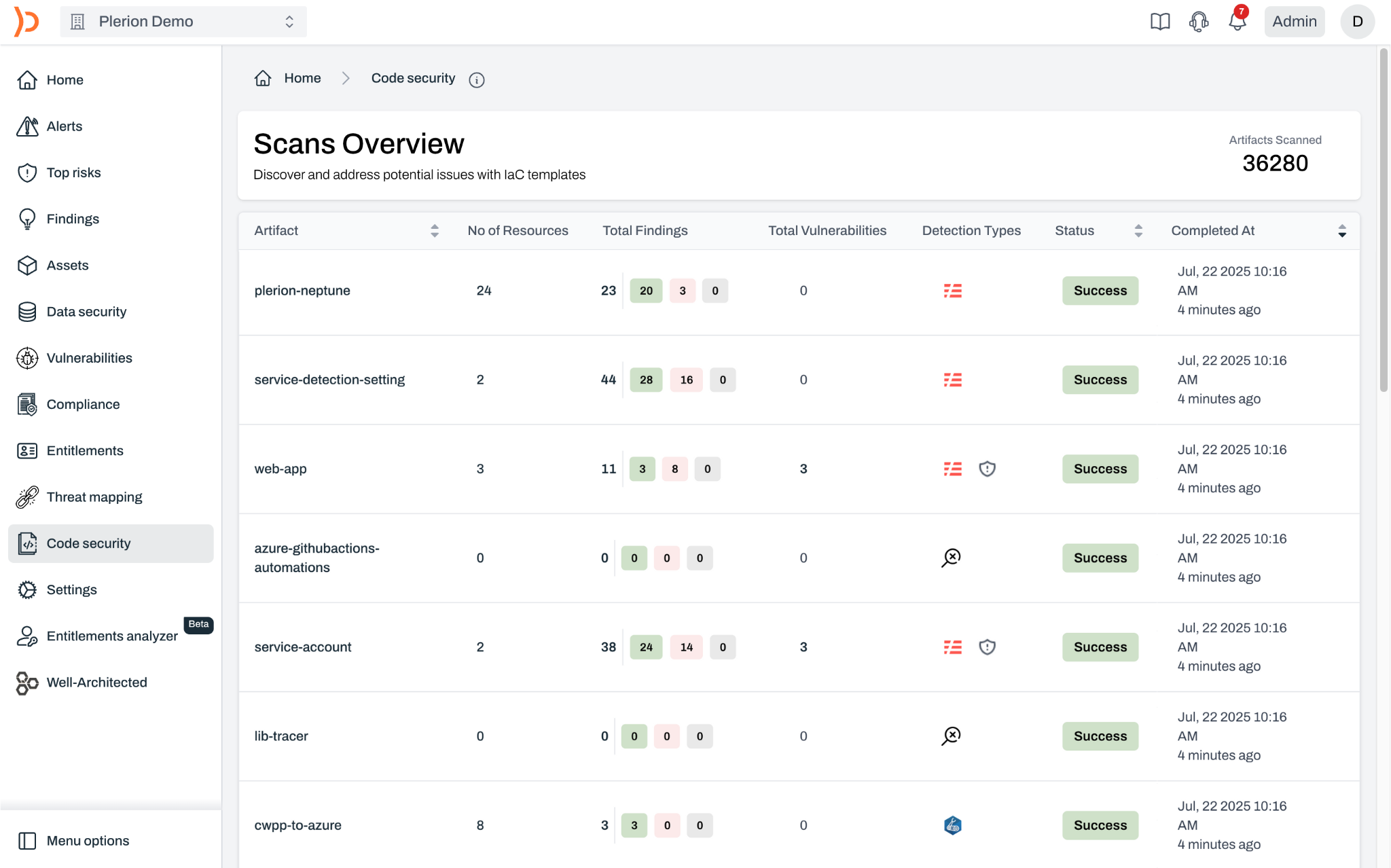
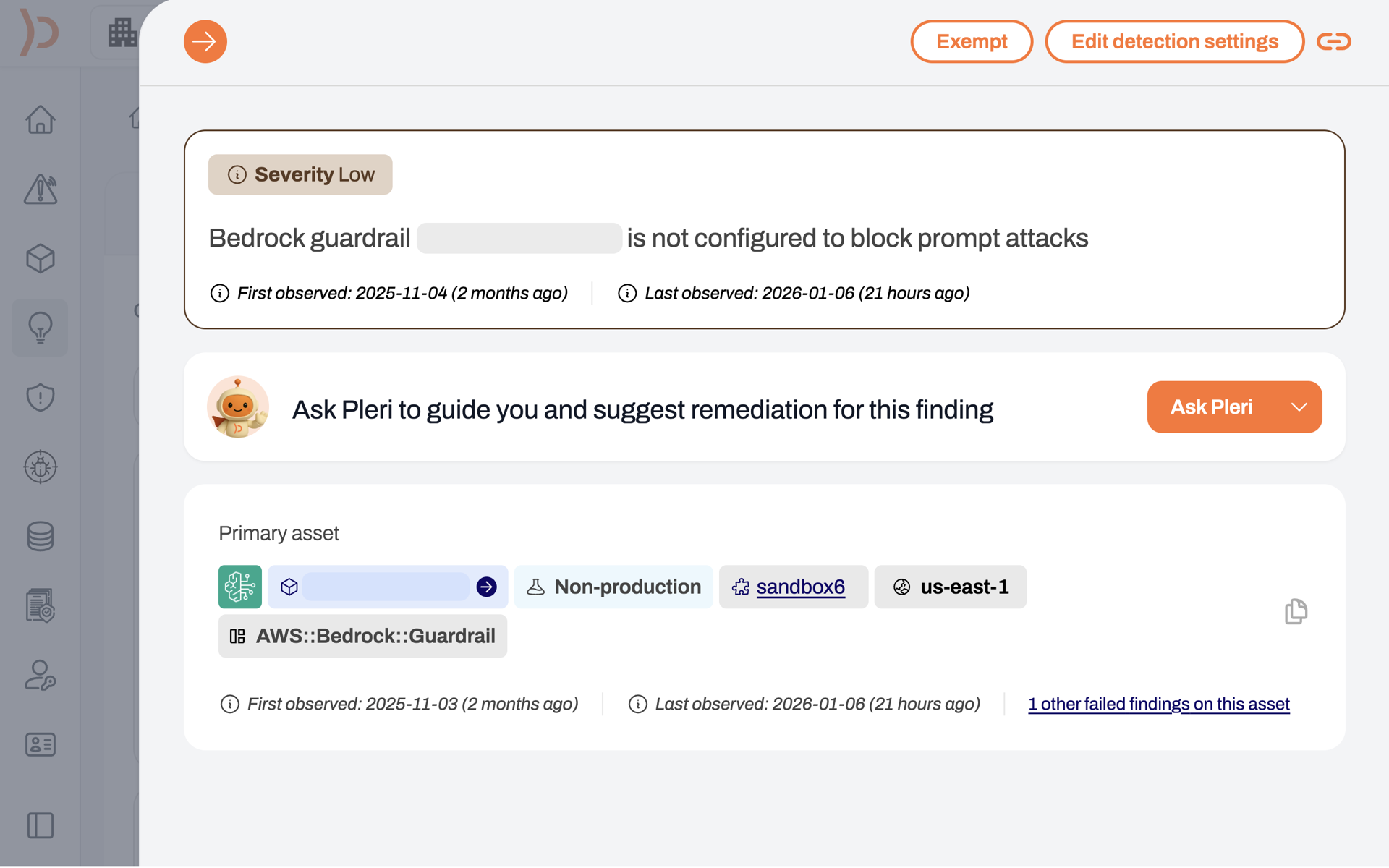
It’s not enough to point to one misconfiguration to figure out if something poses a risk of a breach. For example, an open S3 bucket could be intentionally hosting a public website. The Plerion risk engine enumerates all the factors that influence the likelihood and impact of a breach and displays them for review, so you know exactly why something is a risk.