Gartner would call it a Cloud-Native Application Protection Platform (CNAPP) but we think it's everything you need to secure your cloud.


Gartner would call it a Cloud-Native Application Protection Platform (CNAPP) but we think it's everything you need to secure your cloud.

What you think is in your cloud is often different to what's really there. Identify and query the truth any time with Cloud Asset Inventory.

There are more ways to configure cloud resources than we can count. Find the bad ones with Cloud Security Posture Management (CSPM).

The code running in your cloud is just as important as the configuration. Find vulnerabilities in running software with Cloud Workload Protection Platform (CWPP).

Who has access to what shapes how attackers move around an environment. Limit their options with Cloud Infrastructure Entitlement Management (CIEM).

Everyone has a bad day at some point. Know immediately when its your turn and respond quickly with Cloud Detection and Response (CDR).

Sometimes it's easier to start with the thing you are trying to protect and work backwards. Control your data with Data Security Posture Management (DSPM).

In an ideal world, it's better to stop misconfigurations before they make it to production. Shift left with Infrastructure as Code (IaC) Scanning.

It's not sexy but everyone has to do it. No matter what standard or regulation is important to you, monitor adherence with Cloud Compliance.

At some point someone will ask you what's in your software. Track every component running in your cloud with Software Bill of Materials (SBOM).
In a cloud environment there are usually many hundreds or thousands of misconfigurations, but which of those pose a clear and present danger of a breach? That’s what the Plerion risk engine figures out.


Hackers don’t take the front door. Plerion attack paths show you the sneaky ways they could slip in - so you can block them before they make a move.
There are more ways to configure cloud resources than we can count. Find the bad ones with Cloud Security Posture Management (CSPM).

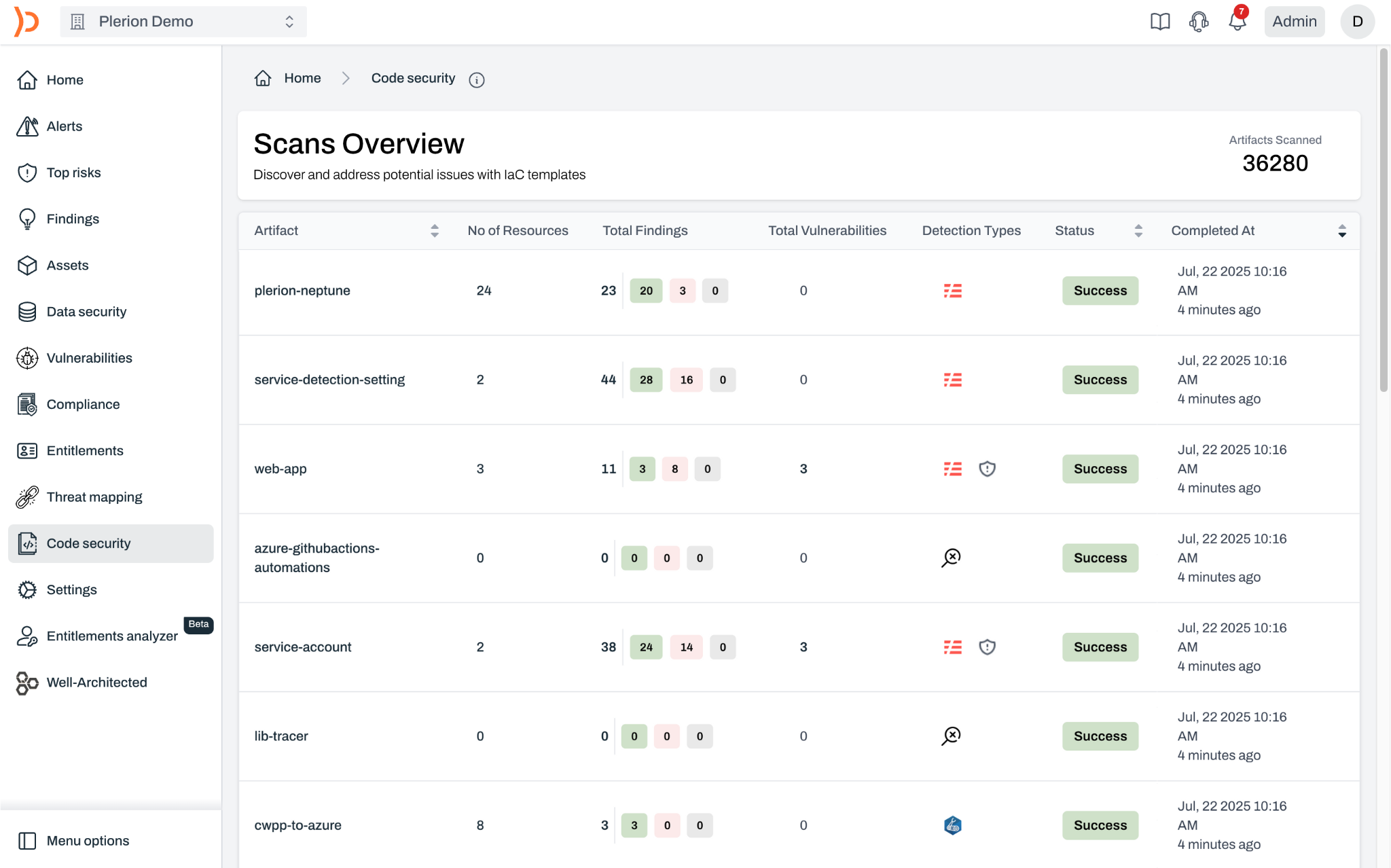
In an ideal world, it's better to identify and fix misconfigurations and vulnerabilities before they make it to production.
The code running in your cloud is just as important as the configuration. Find vulnerabilities in running software with Cloud Workload Protection Platform (CWPP).

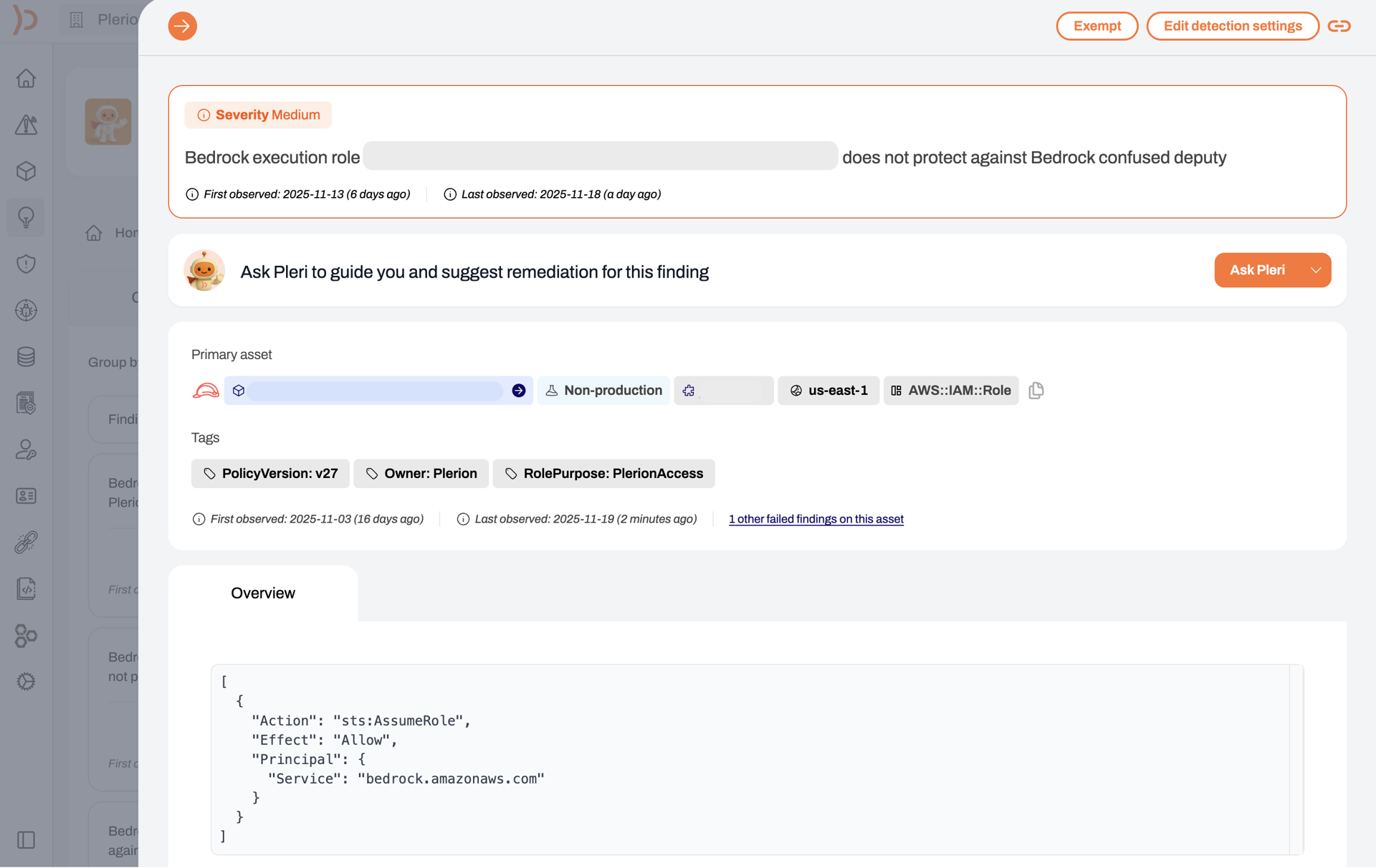
AI is everywhere now; make sure you’re the one in control. With Plerion’s AI-SPM, you get complete visibility into how AI is used across your cloud environments before risks ever creep in.
It's not sexy, but everyone has to do it. No matter what standard or regulation is important to you, monitor adherence with Cloud Compliance.


What you think is in your cloud is often different to what's really there. Identify and query the truth any time with Cloud Asset Inventory.
Some are calling it Kubernetes Security Posture Management (KSPM). We call it finding risk stuff in Kubernetes.


Everyone has a bad day at some point. Know immediately when its your turn and respond quickly with Cloud Detection and Response (CDR).
Who has access to what shapes how attackers move around an environment. Limit their options with Cloud Infrastructure Entitlement Management (CIEM).


Everyone has a bad day at some point. Know immediately when its your turn and respond quickly with Cloud Detection and Response (CDR).
Sometimes it's easier to start with the thing you are trying to protect and work backwards. Control your data with Data Security Posture Management (DSPM).



Risk scores show which assets, accounts and tenants are at risk.

Attack paths highlight realistic ways attackers might access data.

Set thresholds for annoying people based on any finding property.

Filter and sort issues based on whatever matter to you, or the auditor.
