Our infrastructure as code scanning integrates with all major CI/CD tools including GitHub, GitLab, BitBucket, Jenkins, CircleCI, and more. You have complete control over how to action findings - block deploys, display issues, or notify the owner.

In an ideal world, it's better to identify and fix misconfigurations and vulnerabilities before they make it to production.
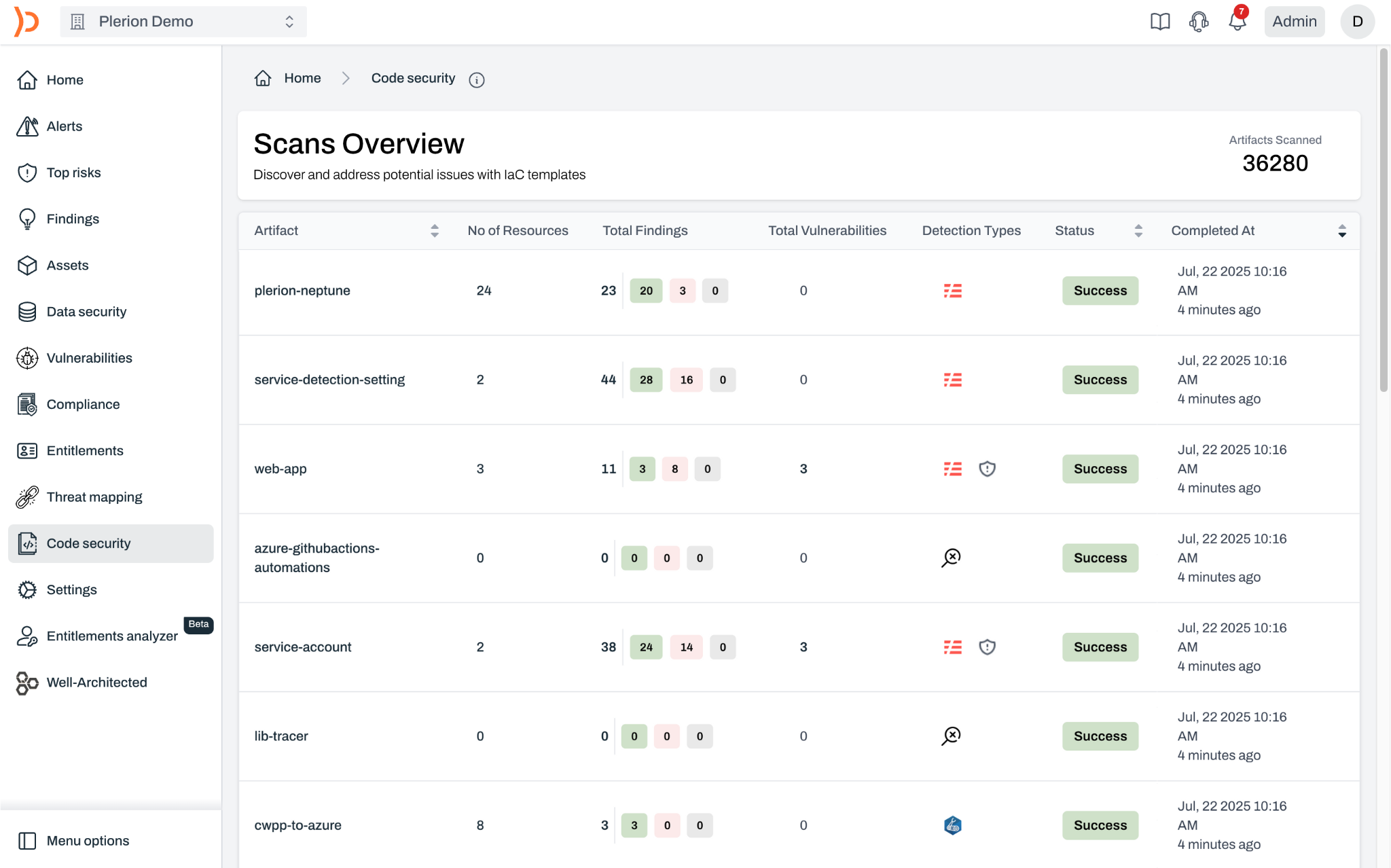
Our infrastructure as code scanning integrates with all major CI/CD tools including GitHub, GitLab, BitBucket, Jenkins, CircleCI, and more. You have complete control over how to action findings - block deploys, display issues, or notify the owner.

You could wait to identify misconfigurations once they are deployed but most of our checks are also available as part of code security. Catch and address any issues that don't meet your risk appetite or compliance requirements before they are in production.

Our code security supports major IaC frameworks including Terraform, CloudFormation, AWS CDK, Kubernetes, Helm, ARM Templates, Serverless framework, and more.

Gartner would call it a Cloud-Native Application Protection Platform (CNAPP) but we think it's everything you need to secure your cloud.



Quickly connect your environment in minutes. Setup is one CloudFormation click away. No security team required.
